Today we live in a world where every business has a website, an online platform, and stores data in the cloud. This has influenced the increase of cyber-attacks on storage and data leakage.
According to Open Web Application Security Project, the top ten security vulnerabilities in 2023 are:
- Broken access control
- Cryptographic failures
- Injections
- Insecure design
- Security misconfigurations
- Software and data integrity failures
Forbes has indicated that, in 2022, high security application development defence methods will be dominated by virtual private networks, role-based access control systems, multi-factor authentication and automated data backup and data recovery systems.
Having a negligent out-look to the above-mentioned threats and web and mobile application protection methods may lead to several vulnerabilities in an application’s security system.
Methods to Protect Applications and Information
Applications used by businesses exchange extremely sensitive data that hackers are continuously looking for. With sensitive data at risk, developers must use specific mobile web application security best practices to safeguard their users and customers.
Securing Mobile Apps Including Flutter Development: Key Practices
Mobile and web applications, especially those developed using frameworks like Flutter, handle extremely sensitive information, making security a paramount concern. Developers must employ a variety of the best security practices for web and mobile applications to protect user data.
Key measures for secure mobile and web app development:
- Secure Code Writing: Writing clean, secure code to prevent vulnerabilities.
- Data Encryption: Encrypting all data, including transmission over networks and local data storage (e.g., passwords).
- Strong Authentication and Authorization: Implementing robust authentication mechanisms and proper authorization settings.
- Network Security: Using secure data transmission protocols like HTTPS and ensuring secure interactions with external services and APIs.
- Abuse Prevention: Validating data on both client and server sides to prevent attacks like SQL injection and XSS, and protecting against CSRF and session manipulation.
- Input Security: Checking and filtering input data to avoid security issues.
- Updates and Maintenance: Regularly releasing updates with vulnerability fixes and maintaining the ability for users to track and update applications.
- Data Separation: Applying the least privilege principle, granting minimal access rights needed for each app component.
- Protection Against Tampering: Utilizing tools for obfuscation and monitoring app vulnerabilities.
Overall, app security is an ongoing process, and developers must continuously update and maintain web and mobile app security best practices throughout the app’s lifecycle.
Who Is Responsible for Cybersecurity and Where Does it Begin?
For a company an information security policy (ISP) is a way of thinking that a business adopts to ensure that its software is created according to web and mobile development security best practices.

It’s Vital for Software Development Organizations to Have an ISP
Security policies are used by technical experts to effectively maintain an application's security, respond appropriately and rapidly to urgent situations, and guarantee compliance with cybersecurity requirements. By doing this, the development company can assure the client that it follows security practices and continually updates and expands its knowledge base.

What is covered by an ISP, and who is in charge of overseeing it?
The ISP of a company specifies the development process and security actions that employees must take:
- Security requirements provide direction on how to make sure an application complies with current security standards. The management of roles and responsibilities, data breach policies, disaster recovery and business continuity plans, secure coding practices, as well as application security monitoring practices and standards are all included in a security policy.
- Internal policies of a corporation govern how employees should behave and act at work. They could include safeguards for individual devices, NDA conditions, restrictions on remote access, and more, along with sanctions for breaking the rules.
- Chief Information Security Officer is the officer-in-charge of carrying out and monitoring compliance with security regulations. The first step in creating a secure application is to create a security policy. The actual development security begins after the requirements are established and the company's experts agree on the dos and don'ts of architecture design, coding procedures, and other issues.
Application Security via Secure Development Lifecycle
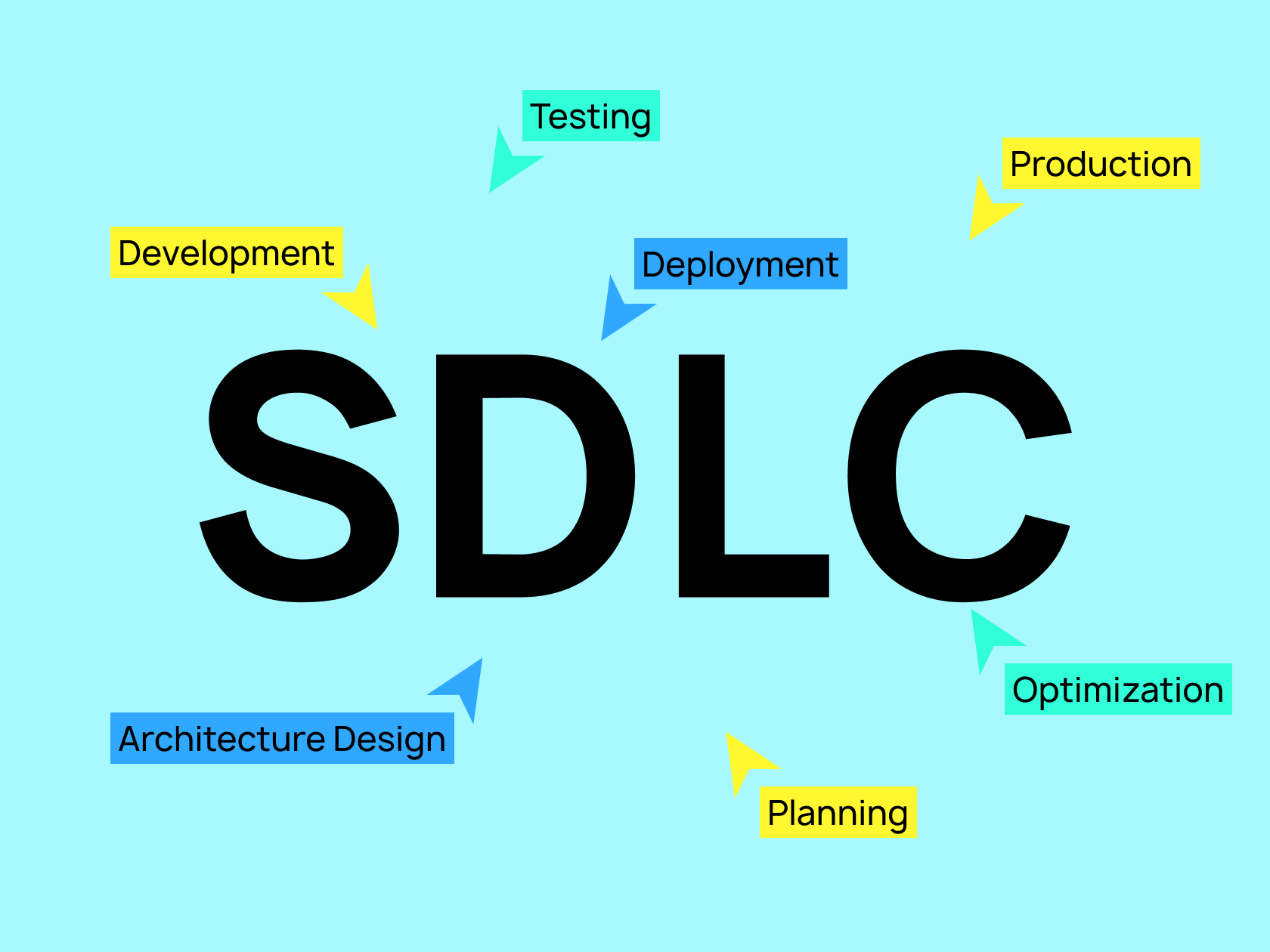
At each level of application development security, specific security procedures are represented by the secure development lifecycle (S-SDLC):
- Planning: Security experts develop a security strategy for the project at the planning stage.
- Architecture Design: Because they provide guidance to the development and quality assurance teams, documentation, risk mitigation techniques, and disaster recovery plans are written out right away.
- Development: The team lead selects a tech stack from the outset, taking into account the needs for storing and acquiring data specific to the product, industry, and region.
- Deployment: Several elements go into creating a solid application infrastructure, and application networks are a significant one of those elements. The majority of the time, application components use vulnerable APIs to transport data. As a result, the system has to be strictly protected.
- Testing: Penetration tests target an application or its infrastructure to assess the security of the system.
- Optimization: Engineers employ specialized approaches that provide step-by-step guidance for each element of a risk assessment to evaluate cybersecurity concerns.
- Production: The program may go to the production stage after being tested and optimized by the development team. A web application firewall will be used to protect it from harmful traffic and distributed denial-of-service (DDoS) assaults.
Security Strategies and Security Design
Choosing the frameworks, languages, and technologies to employ is a part of web and mobile application security best practices. It's critical to identify any unsafe coding techniques that may be relevant to the resources you've chosen.
Certain frameworks might not have the security expertise necessary for your particular environment, or certain technologies might not operate with other security solutions already in use in your company. The security of all technologies selected at this stage and those included at subsequent stages may be in danger if the entire range of ramifications are not taken into account.

During the design stage, pre-existing software development security and application architectural patterns are used. Software architects, for instance, could opt to utilize an architecture framework that permits the usage of current components and encourages standardization.
Developers can consistently address algorithmic issues with the use of tested design patterns. Rapid prototyping, often known as "spiking," is another component of this phase that aids in comparing technologies and locating the best solution to meet the needs that were earlier defined.
The following items are included in the output of the design and prototype phase of the secure mobile application development (or web app development) process:
- Design papers, which comprise a list of all the components and patterns selected for the project.
- Code—a beginning point for subsequent development created by spikes.
App Deployment
Deployment should be as automated as feasible in line with DevOps and cloud native software approaches. Companies frequently execute this phase in a way that delivers software at the conclusion of a specific sprint as soon as it is prepared. However, this strategy shouldn't be used unless security processes and technologies can handle this pace and prevent possible security issues from being introduced into real-world settings.
For business-critical apps or those managing sensitive data, enterprises with lower DevOps maturity or those working in highly regulated sectors may need manual inspection and permission prior to release.
App Security Starts from Great App Development
It's wonderful to use trustworthy and verified security procedures. After experts use these techniques, you must still verify how the program functions. To find these hidden or overlooked security weaknesses, development businesses use penetration testing.
By closing security gaps that potential hackers may exploit, this method aids in protecting the system against actual hackers.
Pentesters employ specialized methods to qualitatively evaluate apps:
- Black box testing is done from the viewpoint of the user to examine both functional and non-functional facets of how an application operates.
- White box testing refers to testing while being aware of the internal workings of the program.
- Grey Box Testing is combining black box and white box testing methods.
- Benchmark testing, which simulates an external hack of the system, is important after the program is prepared for production to guarantee maximum effectiveness.
How WEZOM Ensures App Security with Flutter Development
The Flutter framework is one of our team's frequent choices when developing applications. Here are some of mobile app development security best practices we use when working with it.
- Data protection. For this, we use network traffic encryption, which protects sensitive information transmitted over the network, as well as encryption mechanisms to protect locally stored data, such as passwords and private data.
- Authentication and authorization. We use strong authentication to protect the application when trying to log into it. We also ensure that authorization systems are correctly configured to control access to different parts of the application.
- Network security. To do this, we use secure data transfer protocols such as HTTPS – this helps us prevent the possibility of interception or substitution of data during its transmission. We also ensure an appropriate level of network security when interacting with external services and APIs.
- Prevention of data abuse. We provide data validation at the client and server levels to prevent injection attacks (for example, SQL injections or XSS attacks). We also consider other potential threats, including Cross-Site Request Forgery (CSRF) and session manipulation.
- Secure data entry. To do this, we provide verification and filtering of the entered data in order to prevent the entry of those that could cause security problems.
- Updates and support. Our team regularly releases updates that include fixes for vulnerabilities and other improvements aimed at increasing the level of security. We also ensure the ability of the users themselves to track and download the app updates.
- Data segregation. We apply the "least privilege" principle, that is, assigning the minimum necessary access rights to resources for each application component.
- Protection against hacking. Finally, our specialists use security measures such as obfuscation and monitoring of application vulnerabilities.
Overall, for us, the security of the solutions we create is a continuous process. That's why we maintain and update security measures throughout the entire software development lifecycle.
Conclusion
At this moment, web and mobile app data security is not complete. Additionally, it entails a variety of post-release tasks that experts should handle for the duration of an application's existence. The needs and procedures for security also evolve with the times.

