The modern industry of eCommerce is a huge complex of instruments that are used for increasing sales, growing businesses, and making purchases even more comfortable for clients. But considering the relevance of commercial tasks, business owners can sometimes forget about such an essential component as cybersecurity in projects related to eCommerce, which is a mistake.
eCommerce cyber security is usually based on three factors:
- Privacy: the identity of users is saved and protected by the company.
- Integrity: the data cannot be erased or changed without permission.
- Accessibility: only authorized persons have access to the data.
Today, we will take a look at such vital components of eCommerce as safety, business continuity, and the protection of user data. We will also discuss how modern commercial products are tested for safety.
Why Does eCommerce Security Matter?
What is ecommerce security? Ecommerce security involves adhering to protocols that guarantee secure online transactions. Analogous to how physical stores employ security measures like guards or surveillance cameras to deter theft, online stores must protect themselves against cyber threats.
Online security and consumer data protection are the foundation of cybersecurity. But let’s discuss why is security important in e-commerce in detail and with examples.

There are at least three main reasons:
- Cybersecurity in eCommerce protects the clients’ data
The protection of user data and the safety of the clients constitute one of the highest-priority tasks of the modern business sphere, as client data is a highly valuable asset. At the same time, stolen data may become a serious reputational threat for any kind of business.
Modern cybersecurity measures allow for controlling risks and protecting this data using different methods: from secure payment processing, password policies, two-factor authentication, data encryption, and more.
- Cybersecurity in eCommerce protects from spam and malware
Spam and malware are among the serious threats in terms of online security. Modern methods of ensuring cybersecurity allow for creating preventive protection from numerous types of spam and malware by blocking such dangers from accessing a corporate network, detecting them, and removing them from infected computers.
- Modern cybersecurity instruments protect networks from DDoS attacks
The complex implementation of the necessary safety measures allows for additional protection of eCommerce enterprises from DDoS attacks. DDoS attacks are cyberattacks that imply the flooding of a website with traffic from various directions, which results in it being overloaded. After it, ordinary users cannot get access to it. Secure networks and software that ensure security help companies prevent such cyberattacks or at least minimize their consequences.
Priority of Secure Development and Architecture of eCommerce Platforms
eCommerce is a sphere, in which security is one of the key success factors. Customers want to be confident in the security of their personal and payment data. And the owners of eCommerce projects need to be sure that all of the risks are under control.

Safety needs to be considered during the first stages of design. In addition to this, the approach to this aspect needs to be complex to fit into standards and best practices of security, such as:
- OWASP (Open Web Application Security Project).
- ISO 27001 (Information Security Management System).
- PCI DSS (Payment Card Industry Data Security Standard).
Plus, it is necessary to regularly conduct tests and security audits, use reliable tools and technologies, and conduct training and advanced training of personnel in the field of security.
And the most important thing is that cybersecurity problems in eCommerce are far easier and cheaper when prevented than fixed afterward. The process of fixing them may turn out to be expensive, complex, and time-consuming.
The Role of Professionals in eCommerce Security Solutions
Cybersecurity professionals play a significant role in eCommerce projects, as they ensure the protection of information systems from hacks, data leaks, and cyberattacks. They also help prevent financial losses and risks associated with customer data and increase the trust of the target audience in online services.
The tasks of cybersecurity specialists include:
- The prevention of data loss;
- The protection of users;
- The protection of the organization’s network and data files;
- The creation of the safety architecture;
- Risk analytics;
- Weakness regulation;
- The installation of firewalls;
- The development of safety plans and cybersecurity guidelines;
- The education of staff, technology management, and so on.
So the cybersecurity specialist's main area of work is eCommerce security issues and solutions.
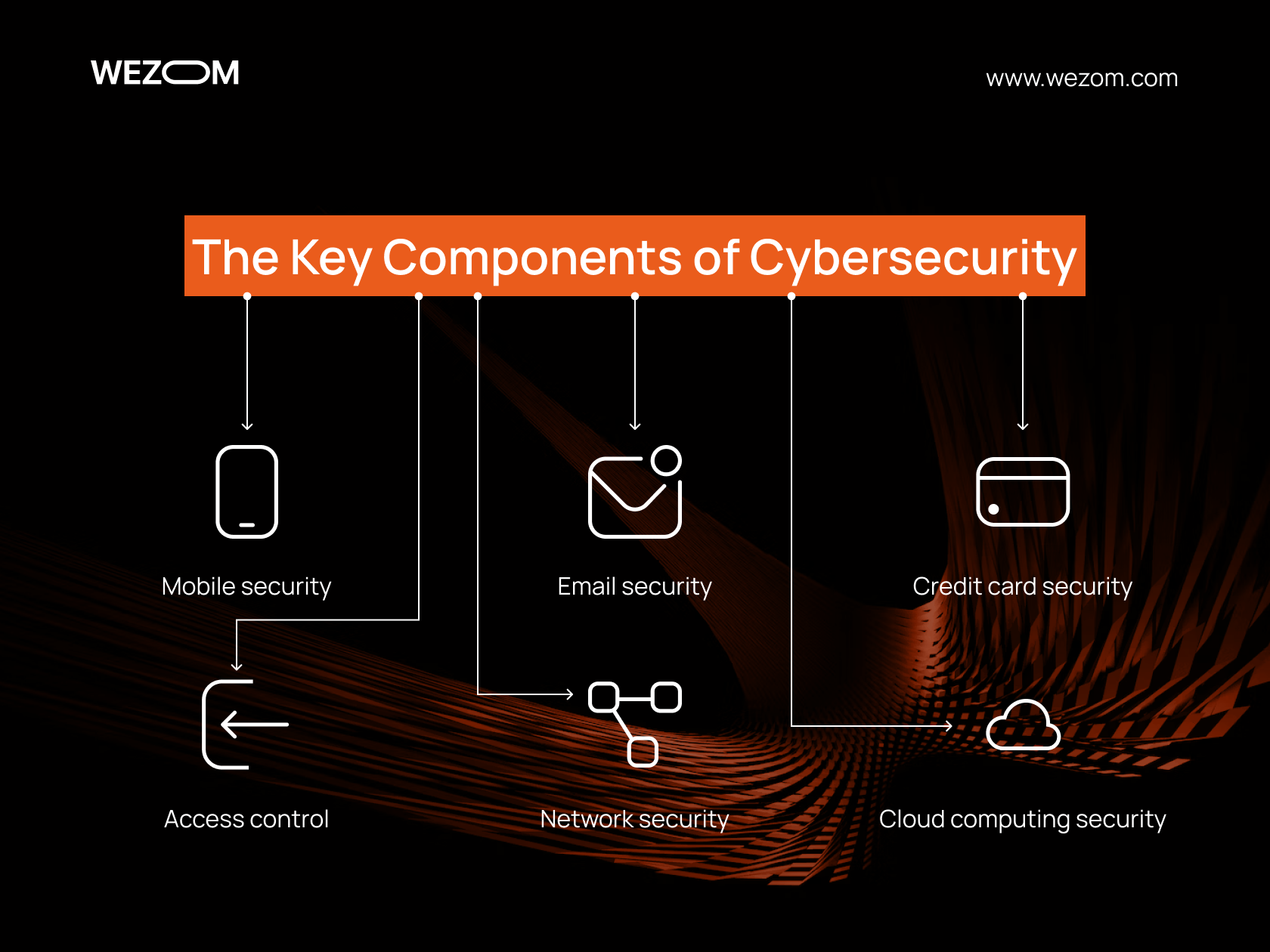
The Key Components of Cyber Security in E-Commerce
Cybersecurity is a complex and multilevel system that consists of numerous components. Here are just some of the examples:
- Mobile security, which refers to the protection of mobile devices, such as smartphones, tablets, and laptops, from malicious applications, phishing, and other threats.
- Email security is the protection of correspondence from unauthorized access, interception, forgery, or destruction. It includes the usage of protected protocols of data transfer, such as SSL or TLS, the encryption of messages and attachments, digital insignias and certificates, and also filtering spam and malicious letters.
- Credit card security is the protection of financial data from theft, fraud, or abuse. The security of credit cards includes the usage of protection technologies, such as chips and PIN codes, the encryption of data during online transactions, such as 3D Secure, cardholder authentication (CVV/CVC codes), and also as well as control over card transactions (SMS notifications or push notifications).
- Access control is the process of defining and restricting who and how can access informational resources, such as files, databases, networks, or applications. Access control includes identifying and authenticating users (for example, using a login and password or biometrics), authorizing their actions (using roles or rules), and auditing and monitoring their activity (using logs or reports).
- Network security is the protection of computer networks from unauthorized access, intrusion, attacks, or data leakage. Network security includes the use of physical and logical security measures (firewalls, proxies, VPNs, or IDS/IPS), encryption of data in transit over the network (SSL/TLS or IPsec), and detection and response to security incidents.
- Cloud computing security is the protection of data and applications that are stored or run in the cloud infrastructure (Amazon Web Services or Microsoft Azure), often enhanced through advanced AES cybersecurity methods to ensure strong encryption and data integrity. Cloud computing security includes the use of cloud and in-transit encryption (AES or RSA), cloud access control (IAM or RBAC), and compliance with cloud data protection standards and regulations (ISO 27001 or GDPR).
Payment Card Data Security Standard (PCI DSS)
If an organization accepts payment cards from popular credit card providers such as Visa, MasterCard, American Express, Discover, and Japan Credit Bureau (JCB), it must strictly comply with the PCI DSS standards:
- Build and maintain a secure network infrastructure.
- Protect cardholder data.
- Manage system vulnerabilities.
- Implement strong access control measures.
- Monitor and test networks.
ISO 27001
ISO/IEC 27001 is an international information security standard developed jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It defines the requirements for an information security management system that must protect the confidentiality, integrity, and availability of information in an organization.
Compliance with the ISO 27001 standard provides organizations with several important benefits at once:
- Increasing the confidence of customers, partners, and stakeholders in the information security of the organization.
- Reduced loss and damage from security breaches or other incidents
- Data Protection Compliance.
- Improving the competitiveness and reputation of the organization.
- Optimizing business processes and improving management efficiency.
But here it is also important to understand what types of information e-commerce sites need to protect.
Best Practices for eCommerce Security Testing
Companies that specialize in cybersecurity use different verification methods. Therefore, we will consider the one that we use ourselves and which has proven itself well in practice.
The work consists of three main steps and several stages in each of them:
- Preparatory stage
- Primary preparation. We discuss the client's business goals and requirements to understand what threats may arise. We also determine the area of testing and select the appropriate tools.
- Collection of information. Our experts collect product and system information to understand how it works and identify potential threats.
- Hypothesis testing
- Conducting pen-testing (Pentest) using a "black box". First, we simulate the actions of intruders without knowing the internal structure of your system. Then we deepen the study based on the results obtained.
- Evaluation of results. We evaluate and analyze the received data, confirming or refuting our hypotheses, as well as identifying vulnerabilities.
- Suggestion of solutions
- Development of strategy and recommendations. We develop a strategy individually, based on the data received. The goal is to eliminate or minimize discovered vulnerabilities.
- Solution implementation. At this stage, we implement the developed strategies and security measures to strengthen the protection.
Conclusion
Cybersecurity in e-commerce projects is not just a mandatory component of modern business activity, but also an important competitive advantage. However, you must remember that no cybersecurity system provides absolute protection. Therefore, it is necessary to work on security constantly and comprehensively.
By protecting your customers' data, you increase their trust, loyalty, and satisfaction, reduce financial losses, costs, and reputational risks, and prepare for new challenges and opportunities in the world of e-commerce. We recommend that you pay more attention to this issue and, if necessary, contact our experts.
