The popularity of APIs, also known as Application Programming Interfaces among enterprise mobile app development companies, is linked to the fact that enterprises started choosing them for delivering new products. Nowadays there are over fourteen thousand public APIs available, but just knowing them is not enough to use them properly and securely.
Since the API, or Application Programming Interface, is responsible for so much of what concerns the security of your mobile application as a whole, it is important to pay enough attention to this small aspect to save yourself from a lot more risk in the future. APIs are complex and problems can be, too.
It needs to be remembered that, along with the benefits APIs provide to developers, there are also security issues and other problems. So, by carefully considering them, you do yourself a big favor. So, let's look at what factors guide the process of choosing an API and how easy it is to protect yourself.
How Does API Work?
Any application either needs a web panel, third-party web services, or an API. Application programming interfaces are created as a set of instructions and defined standards that have access to any web application. So basically, in custom mobile applications development, the need for APIs is due to their mechanism of work. But along with the growing popularity of application programming interfaces, new challenges arise.
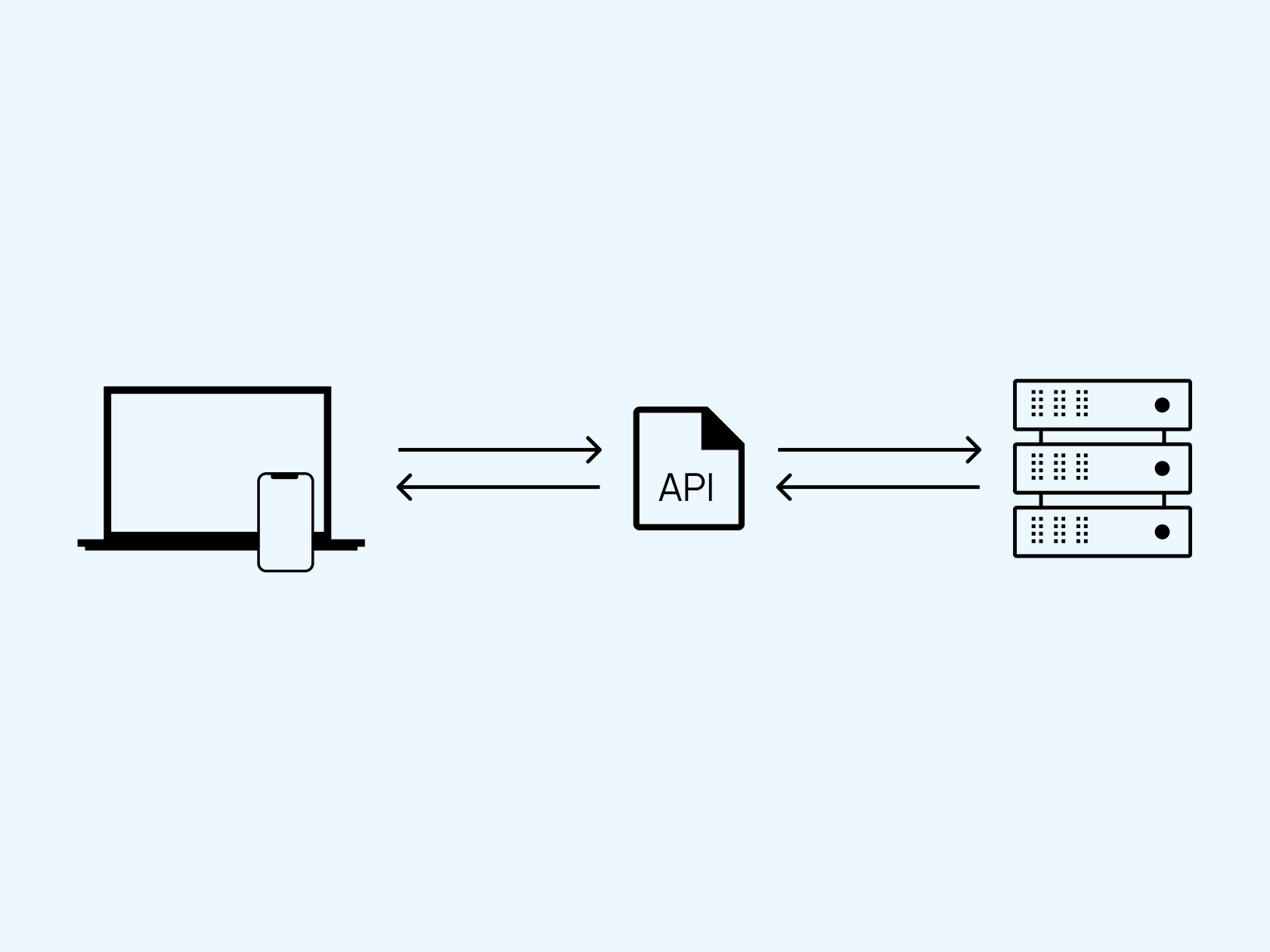
When we choose an API library, we often ask ourselves whether it does its job well or whether it is reliable and suitable for our application,but “Is it not vulnerable?” should be one of the most prominent questions that come to our mind.
The Need for APIs in Custom Mobile App Development
APIs allow developers and mobile development companies to integrate services in their apps with the help of third-party service providers and not to create their own. APIs have served developers for a long time in working with different software. For ensuring a sufficient level of security, the APIs need to be implemented properly and they also need to suit your application.
What is API Security?
The aspect of security is vital for APIs and needs to be considered by mobile development companies in the process of choosing libraries. It is crucial to evaluate all the risks before deciding whether to use an API for a particular task.
Generally, all applications are created with basic security principles considered in the process of development.
Some of these principles include:
- Least privilege.
- Defense-in-depth.
- Minimized attack surface.
- Client trust.
By making your applications secure, you not only invest in user trust but also in device integrity. For APIs, security is essential as they are closely interconnected with the other aspects of the application’s work.
When choosing a suitable API for your mobile application, read about different options and compare them to make your own conclusions about security. Application programming interface reviews can help you in this pursuit as you will learn a lot of useful information. Don't rely on the first API you see: a thorough analysis will save you a lot of nerve.
The field of web API security includes the aspects of privacy, access control, and also of detection and resolution of common attacks against APIs. The app itself is targeted at employees and customers. The customer component of the application is connected to the server side with the help of APIs.
The Potential Risks Associated with APIs
As APIs become more widely used and gain popularity in mobile application development, attacks against them become more frequent. Some experts suggest that attacks against APIs will be one of the most pronounced threats in the future of cybersecurity, so application programming interfaces cannot be said to be safe.
Many mobile app development companies in the USA are now increasing the degree of protection because the threat to API is also a threat to the company's activities. This necessity to pay attention to security measures is exactly the reason why WEZOM offers secure and robust solutions that will help you protect your APIs, as well as your applications in general. You won’t have to worry about the fact that the API aspect will put the safety of your entire application at risk.
Some of the Common Attacks Against Web APIs
When it comes to attacks, APIs may be subject to attacks from most of the same networks and web app attacks. Some of the most frequent types include:
- Mitigation.
- Injection.
- Cross-site scripting
- Distributed Denial-of-Service, or DDoS.
Using protective measures will help you handle almost all commonly occuring types of attacks.
Best Practices for API Security for Creating Secure Mobile Applications
As there is a range of security best practices emerging and developing, professionals need to pay attention to these innovations and ways to provide themselves with much-needed security.
What Would We Recommend for Ensuring API Security?
For API security when creating mobile applications, you can apply the following recommendations we use in our work:
To achieve secure communication, you need to use HTTPS instead of HTTP. Authentication and authorization are necessary to ensure that only authorized users have access to data. Also, you need to restrict access to API functions to only necessary operations, so make sure that happens too. Finally, it’s recommended to protect against session hacking by using cookies or tokens for user authorization and identification.
To protect your application and API against DDOS attacks, you should ensure that the database used by your program is protected from unauthorized access. Access restrictions and data encryption can help achieve this goal. To identify potential security issues in your application and API, perform a vulnerability analysis. Use standard protocols such as OAuth2 to ensure secure communication between your application, users, and API providers.
It is important to understand that using API Gateway is not the only solution for API security. It is recommended to use many different technologies and methods to ensure the maximum security of the application.
Application Security and Application Programming Interfaces
APIs allow the realization of a range of tasks while the deficiency of easily accessible APIs for the Internet and the market results in disturbance in security and loopholes that companies can use. API interfaces allow unauthorized and external individuals to get access to the application’s data.
- Are these risks worth solving a particular problem?
- Or in any case, is there no alternative to the API, if a certain development needs data that can only be obtained through the API?
- Have there been cases when due to the use of the API in our projects there was a data leak?
Generally speaking, as APIs are useful for applications, you just need to consider the security measures when choosing them. And there are concrete security practices that need to be followed.
What APIs and API libraries do we most often use in mobile development? How do these APIs affect the overall security of the application?
There are many APIs and API libraries used in mobile development, but some are more common than others.
Below are the most commonly used APIs and API libraries in mobile development:
The Google Maps API is a tool used to integrate Google Maps into mobile applications. It allows users to search for places, display directions and get other information about the area. One of the main advantages of the Google Maps API is its wide distribution and the possibility of using it in various applications.
Google Cloud Messaging (GCM) and Firebase Cloud Messaging (FCM) are notification services that allow you to send messages between a server and a mobile application.
Facebook API: This API is used to integrate Facebook features into mobile applications. It allows users to log in with Facebook, post and view posts, get information about their friends, and much more. Facebook API has a large user base, which makes it popular among developers.
Firebase API: This API from Google is used to build the backend and various functions like authentication, database, analytics, cloud storage, and many more. The Firebase API provides a convenient interface for developing and managing applications.
Each of these APIs and libraries can affect the general security of the application if are not used correctly.
As an example of such problems, if Google Maps API shows sensitive information, such as users' locations, on a map, it puts the application at risk. However, if the API is used correctly and safely, it should not adversely affect the security of the application. The main point here is that developers need to use security best practices and it is a must for keeping the application secure.