A Mastercard survey of more than 5,000 small and medium-sized business owners across four continents found that approximately 46% had experienced a cyberattack, and nearly one in five of those affected subsequently had to declare bankruptcy or close their business. At the same time, based on our experience, many SMB representatives still mistakenly believe they are of no interest to cybercriminals. That's why we decided to share our small business cybersecurity tips in this article.
The Rising Cybersecurity Challenges for Small Businesses
With the adoption of cloud solutions and online services, businesses are becoming increasingly vulnerable. In particular, because employees often access corporate data from public locations using personal devices without proper security settings, the boundaries of the corporate network are erased. If we add to this the growing number of attacks on business software vendors, it becomes clear that even if you only have 10-20 employees, you must approach risk management as systematically as a large corporation.
It's also worth noting that hackers don't have to do much effort to attack a small company – such businesses typically lack sophisticated intrusion detection systems, rarely use encryption, and often blindly trust their contractors to keep corporate information private. In turn, all these weak links can easily become targets for attackers.
The most common threats today include:
- Phishing emails;
- Malicious attachments;
- Fake websites designed to steal private data;
- Ransomware.
Attacks via instant messaging apps and social networks, personal devices, and Wi-Fi hacking have also become common, so we'll discuss how to prevent them with our cybersecurity best practices for SMB below.
Building a Strong Cybersecurity Foundation
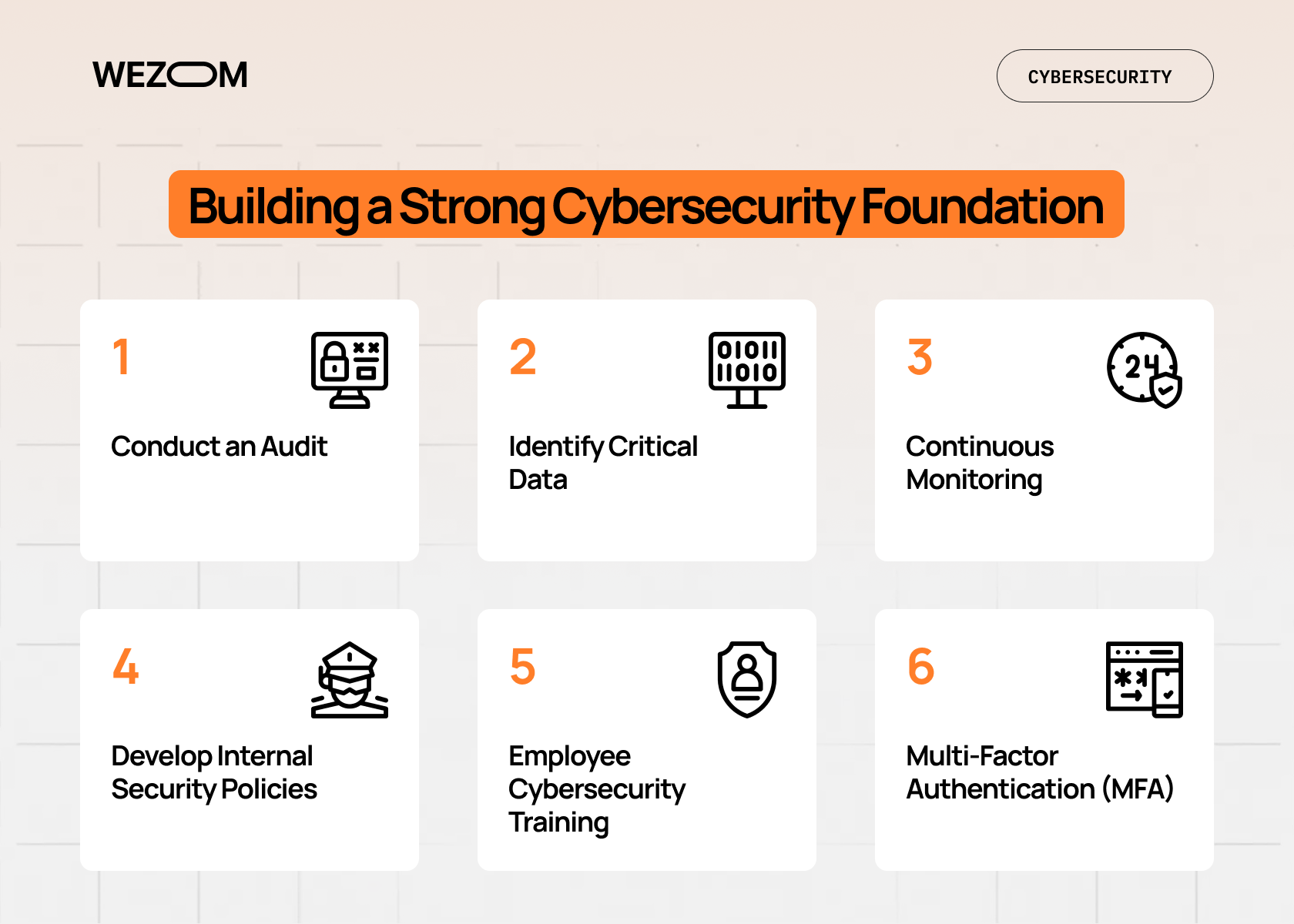
Let’s start our cybersecurity guide for startups with stating the fact that whether it’s on-premise or cloud security for small businesses, it should still begin with an audit – i.e., determining which devices, programs, and accounts are used. Next, you’ll need to identify critical data (to restrict access to it) and implement automatic backups and data encryption. And, finally, you’ll have to set up 24/7 monitoring.
At the same time, to ensure that all these measures are not implemented haphazardly, you must develop internal security policies – a document that describes who works with corporate data and how, which devices are allowed to access the network, how passwords are stored, and who is responsible for incident response.
It's also important to remember that the main risk is the human factor – which is why cybersecurity awareness training for employees (including remote ones) is so crucial, for example, through phishing simulations, pentests, and email reminders. For these same reasons, it's important to take into account the need for multifactor authentication, which, as practice shows, can prevent 90% of password-theft attacks. We typically set it up for all business services, including corporate email, CRM, cloud storage, primarily using dedicated authenticator apps like Google Authenticator instead of SMS, as they are more secure.
Essential Cybersecurity Best Practices for SMBs
Effective cybersecurity is always a systematic approach. For example, we always adhere to the "least privilege" principle, assigning access rights to users only to what is necessary for their work tasks. Another important aspect is regular updates and security patches, especially for network devices and CMSes. We also strongly recommend limiting the use of flash drives and external storage devices and implementing real-time backup controls.
Encryption deserves special attention in all of this, as it ensures that even in the event of a leak, data remains useless. Most often, we resort to two-layer encryption: at the device level and at the file level. Backups should also be considered, preferably following the "3-2-1" rule, which implies creating three copies on two drives, one of which is located off-site. It also makes sense to initially consider cloud backup solutions for SMB.
Now, a few words about vulnerabilities – the fact is that SMB companies use standard routers without security settings. To minimize risks, our experts always perform secure Wi-Fi setup for businesses and allocate a separate network for guests and IoT devices. We also install managed firewalls with IDS/IPS functionality so they can independently analyze traffic behavior and identify anomalies. Finally, we ensure regular updates by implementing centralized update tools and monitoring security patches across all devices.
Practical Small Business Security Checklist
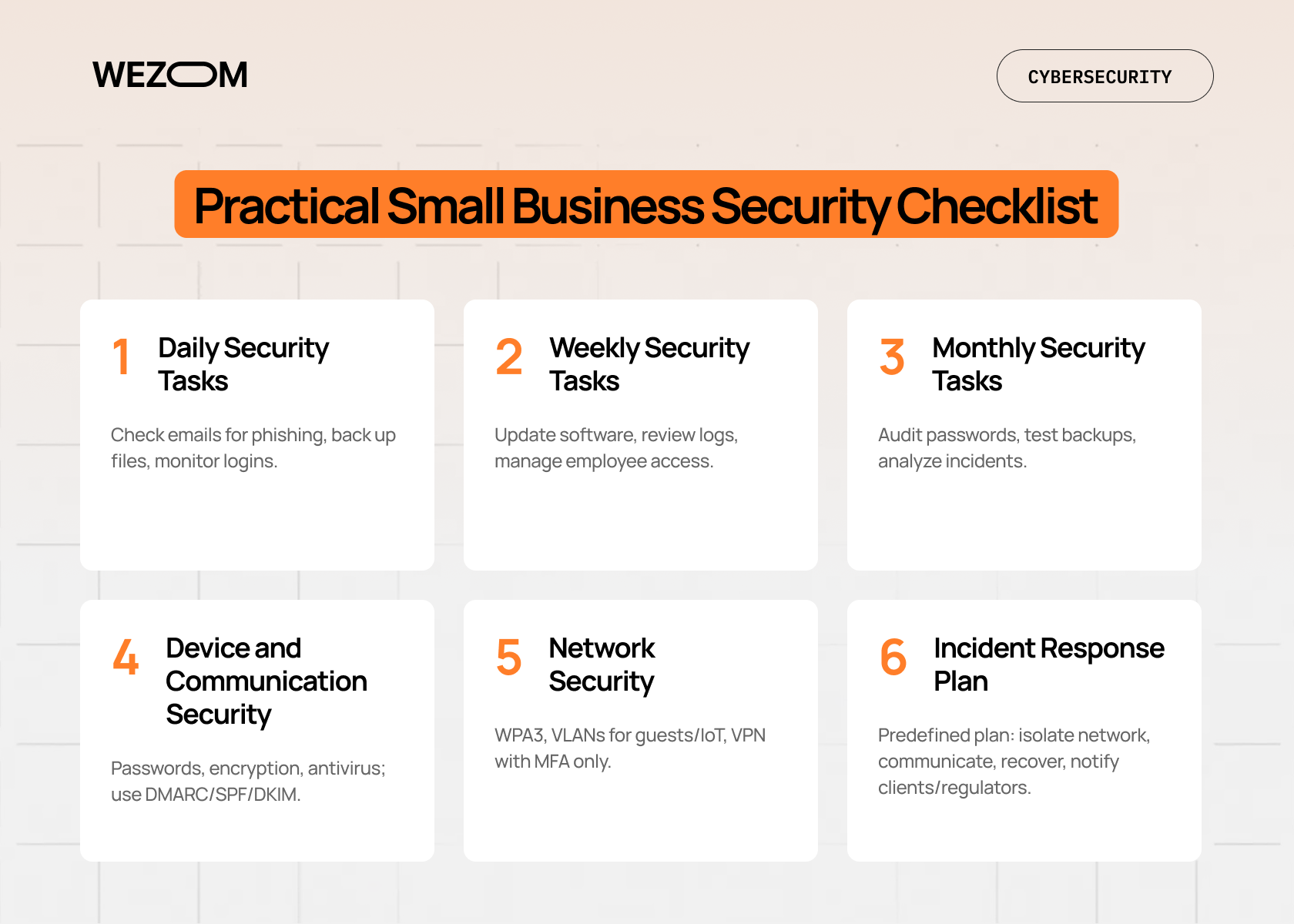
Without constant monitoring, protecting small business from cyber attacks becomes ineffective. Here's a small business security checklist to help you achieve this "consistency":
- Daily check business emails for phishing messages, ensure critical files are backed up, and monitor login notifications;
- Weekly check for software updates, logs, and employee access control;
- Monthly audit passwords, test backup restoration, and analyze incidents.
It's also worth noting that business security depends not only on the software it uses but also on devices, communications, and the network. Here's why:
- All laptops and smartphones should have passwords, configured encryption, and an installed antivirus with centralized management;
- For phishing protection for small business, they should use DMARC, SPF, and DKIM to prevent sender spoofing;
- A small business network security with WPA3, separate VLANs for guests and IoT devices, and VPN access only via multifactor authentication, is required.
Finally, if a data breach does occur, a pre-prepared incident response plan should be brought to life. This plan includes responsibilities, a sequence of actions (including isolating the network and disabling its compromised components), communication methods, and recovery steps. It's also important to consider the legal aspect of this plan, specifically the on-time notification of clients and regulators in the event of data loss.
Cost-Effective Cybersecurity Guide for Startups
Startups often think they'll have enough time to implement security later, but at the start, they can build an architecture with minimal investment. This includes wise choosing cloud services, implementing multifactor authentication, ensuring backups, and setting up login monitoring.
For example, today, there are many affordable cybersecurity solutions for SMB that don't require large budgets or are even free. Specifically, our top cybersecurity software for startups is:
- Bitdefender GravityZone (an affordable antivirus for SMB);
- ProtonMail (encrypted email);
- Cloudflare (for website and VPN access protection);
- CrowdStrike (one of the greatest endpoint protection tools for SMB);
- pfSense (one of the best firewalls for small businesses);
- OSSEC (intrusion detection system);
- Wazuh (security monitoring);
- KeePassXC (password manager).
The main thing in their effective use is proper configuration and regular administration.
Ultimately, for small businesses without an in-house IT department, it makes sense to delegate IT security tasks to professionals. These companies typically provide 24/7 monitoring, patch management, incident response, and security audits. Actually, we are one of these companies, so you can hire a cybersecurity consultant for SMB; right now; also, you can learn more about how we provide managed security services for SMB here.
Protecting Your Small Business from Cyber Attacks
The primary goals of any security strategy are both preventing attacks and minimizing their impact.
In particular, since phishing is considered the most widespread type of cyberattack, you should implement employee cybersecurity training for small business to recognize this attack type promptly: typically, these are errors in email address, unusual links, and urgent requests. It also makes sense to use anti-phishing filters and training simulations. If an attack does occur, you need to train your employees to respond immediately: isolate the device, change passwords, and notify IT specialists without hiding the incident.
Meanwhile, proper ransomware prevention for SMB is achieved through regular updates, backups, and limited access rights. For enhanced security scenarios, we also recommend implementing a "read-only" policy for critical data, creating isolated backups that aren’t accessible through the network, and, of course, training employees.
Another important aspect is ensuring reliable customers' data protection for small businesses, as it’s the most common target for attacks. For example, we protect this data in accordance with PCI DSS and GDPR principles, introducing encryption during transmission and storage, strict access control, and regular pentesting. Additionally (for the eCommerce sector), we ensure payment gateway protection, card tokenization, and transaction monitoring for suspicious activities.

Future-Proofing Your Small Business Cybersecurity Strategy
Cybersecurity for small businesses should be proactive and not just respond to threats – it needs in the implementation of a resilience strategy (which, in practice, means designing the IT infrastructure so it can adapt to new threats without a complete rebuild) – minimizing manual processes, auditing the security of new software, and implementing smart monitoring tools.
Particular attention to security should be paid to companies operating in the cloud. For these clients we implement zero-trust principles, mandatory multi-factor authentication, and cloud security policies, clearly defining who manages encryption keys, who has access to administrative panels, how backups are created, and who controls the access log. Such businesses also have to ensure legal compliance (we're talking about GDPR, CCPA, and similar regulations) – here, implementing compliance-by-default rules can help. These rules typically include storing the smallest possible amount of data, automating access notifications, documenting information processing operations, pentesting, planned cyberattack simulations, and so on.
Finally, it's worth noting that cybersecurity must grow with your business. This means that a strategy for a company with 10 employees will quickly become ineffective and unprofitable when they grow to 100, unless it's scalable from the start. That's why such businesses should use centralized control panels, automate access policies, and deploy cloud-based SOCs from the outset.
FAQ
What are the first steps small businesses should take to improve cybersecurity?
It's important to start with an audit – it will help you understand what types of data are stored, who has access to it, and where this data is vulnerable. Next, you'll need to set up backups, multifactor authentication, and a basic small business password policy.
How can startups protect customer data without overspending?
It makes sense to use cloud solutions with built-in security (such as AWS or Google Cloud), enable data encryption, and configure access rights – this will be much cheaper than fixing data leakage consequences.
What role does employee training play in small business cybersecurity?
This role is critical, since approximately 80% of incidents are caused by human error. In turn, training employees to recognize phishing, create strong passwords, and work securely with corporate systems can significantly reduce these risks.
Are free cybersecurity tools effective for protecting small businesses?
Yes, free cybersecurity tools for startups like Wazuh or pfSense can provide a high level of protection if properly configured by a specialist and updated regularly. By the way, you can buy managed security services at WEZOM.
How often should a small business update its security checklist?
This should be done at least quarterly, as new threats are constantly emerging (updates should also be performed promptly after any changes to the IT infrastructure).
What is the most common cyber attack on SMBs today?
In our experience, the most widespread cyber threats to small businesses are phishing (extorting data through fake emails) and ransomware (locking files with ransom demands).
How can remote employees be included in a cybersecurity strategy?
For remote employees, you’ll need to provide VPN access, set up mandatory multifactor authentication, and implement device encryption. You should also create security policies for off-site work, specifically defining which networks are allowed and how data should be stored.

