The importance of data security has long been discussed among large corporations and companies. This topic became especially relevant after the digitalizing boom in 2020, when most companies moved all of their workflows, information, and communications to online platforms. Before that period, storing information on cloud servers was also quite popular. Storing information on a cloud server is absolutely commonplace for large companies, but how secure is it?

Logistics companies are no exception. Information leaks can have consequences such as the loss of large sums of money. The loss may not be felt immediately, but an audit at the end of the quarter may reveal that loans have been taken out on your company or that a large sum of money has been lost. The financial issue is very unpleasant in such a case, but even more difficult when classified information "leaks" out of your company. This may be especially pleasing to your competitors or other organizations but is unlikely to be good for your company.
What to do with the data secure, how to store it so that it is safe from leakage, and what is the real risk of a data leak at your company? In this article, we will answer all of these challenging questions.
Why Data Security is Important in 2022
Usually, people do not pay much attention to their cloud data security. Nevertheless, almost every second phone user has a password when unlocking the screen. This is the simplest example of how every day we try to protect our privacy.
If in the example of individuals, a password on the phone is data protection too, then speaking of large companies, things would be a little different. The damage from a data breach can be dangerous because of your confidential information loss, which can hurt your reputation, loss of bank account information, and leakage of your personal technology and more. In the case of a bank information leak, you could get a loan you didn't take out (their worst option) or your competitors could just know more about you with your banking history. Both options are unpleasant, but these aren't the only examples of what can happen to your company if your data isn't protected.
Types of Cybersecurity in the Logistics
There are 3 basic types of protecting your information on servers. But we have highlighted those basic ones that will help protect data from logistics company cyberattack.
Access Control
The name already speaks for itself. To gain access to the data, users must be verified, or validated, in order to prove that they can access the data. This type of protection also includes two-factor verification along with a username and password.
Backups & Recovery
No one is immune to global disasters. A war, earthquake, flood, or storm can harm data stored in a disaster area. To insure yourself against unplanned incidents, create an additional drive (physical) so that you don't lose your data.
Encryption
With personal software, you can hide your data by encrypting letters and numbers with proxy symbols. The trick is as follows: even if an unauthorized user accesses this data, the symbols will still represent incomprehensible characters to him. But for authorized users, the information remains the same. With this protection, you can encrypt anything from general information to mailboxes.
In any case, for quality logistics cybersecurity, encryption of information will be quite enough for you. For full confidence, you can also set up two-factor authentication, create regular backups, and share your information across multiple servers.
Data Security for Logistic Company
If we talk specifically about data protection for a logistics company, then you should definitely think about your software – a TMS application. Let's take the situation as an example of two companies. The first company paid a regular subscription to use the TMS application. It didn't have its development or own software, so the company kept the data on its server. Since the software company's server is insecurely protected, and the logistics company stores all of its important information in the app, the company risks several thousand dollars in damages as well as a ruined reputation in case it leaks. And don’t forget that company’s clients will suffer from this accident too.
The second example: the company uses proprietary software, and accordingly, all of its data is stored on a single server, which is securely protected. In this case, the data are exposed to much less risk, and to be quite precise, we can say that the data is fully protected.
3 Ways to Protect Your Data
Once you've determined for yourself that your data should be protected, it's time to determine how you can do it and how logistics security works.
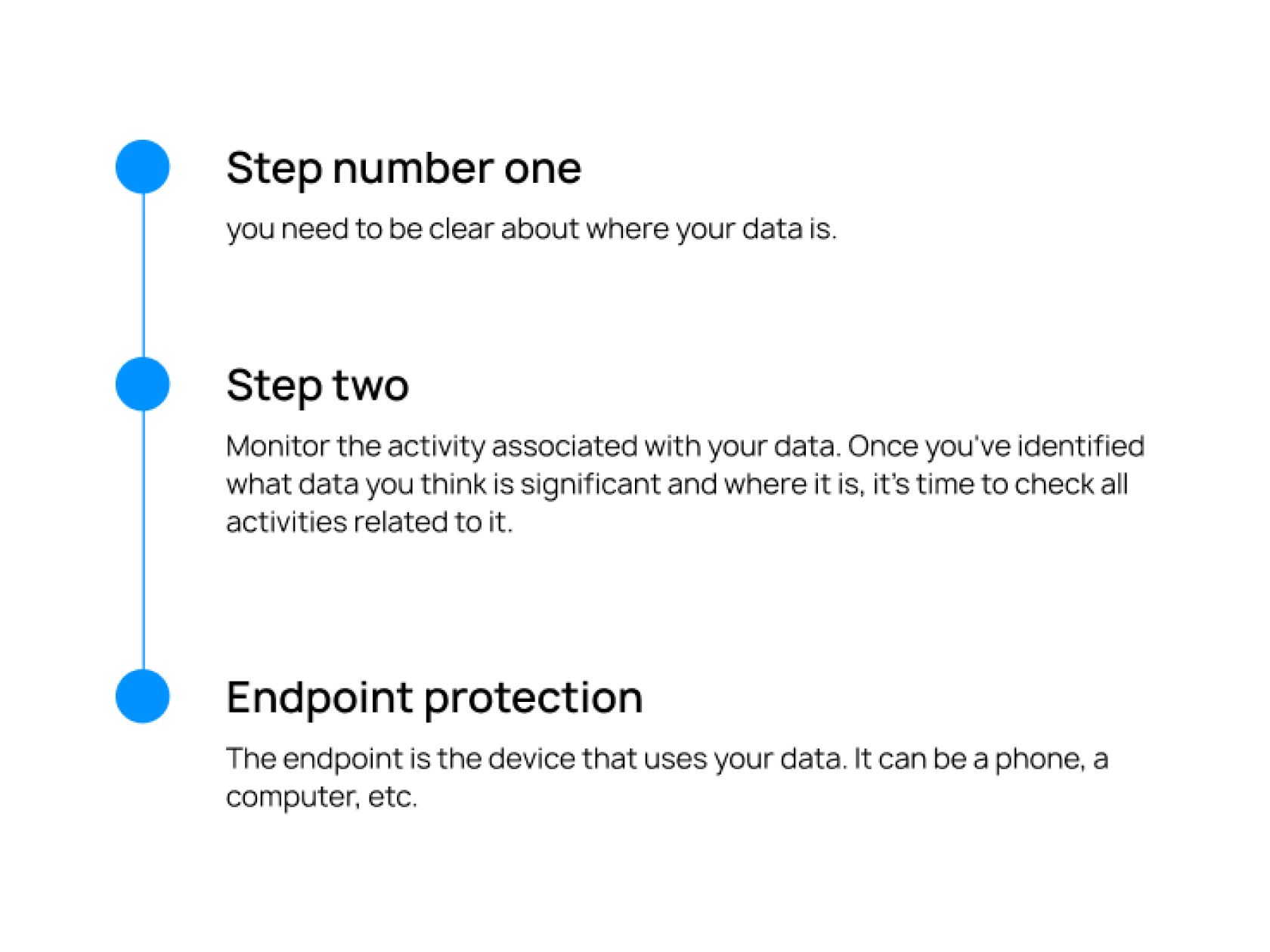
- Step number one – you need to be clear about where your data is. Many corporations and companies simply lose sight of all their important information and numbers. But how can you protect your information when you don't even know where it is? Gather all the right data you need to secure in one place.
- Step two. Monitor the activity associated with your data. Once you've identified what data you think is significant and where it is, it's time to check all activities related to it. Observe who has access to them, and how often they are accessed again. If there is any suspicious activity associated with them, etc. This information can help you determine exactly what data you need to focus protection on.
- Endpoint protection. The endpoint is the device that uses your data. It can be a phone, a computer, etc. The more devices that have access to your data, the riskier it is. It is much better and easier if your company uses a single system for transferring data or company-issued devices. Such measures can save your data and prevent major losses.
Avoid Data Leakage with Wezom
A thousand words aren't enough to tell you the full story of how you can secure your data. In a free webinar from Wezom, you can learn more about this topic and talk about it with the company's leading experts. We can explain this in more detail in a free Wezom webinar, which will take place November 22 at 10 pm by Chicago. Register for the free webinar by the link and let’s improve your data security!