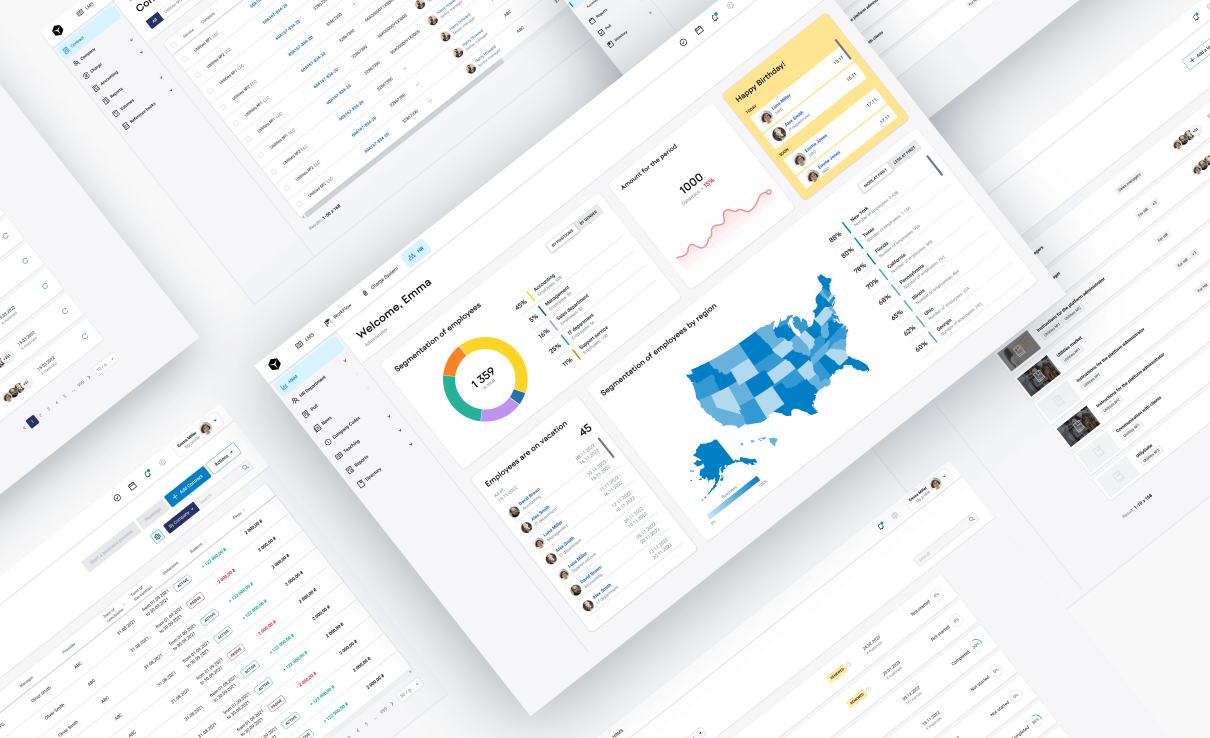
How we analyzing a digital company for weaknesses with our service Cybersecurity in eCommerce

Contactless vehicle rental service
Our client is an international organization that offers personal vehicle rental services online. The company owner reached out to us due to the suspicion that a data leak may have occurred in the company.
This is why the client’s web service should have been checked for vulnerabilities that may lead to user data losses, confidentiality violations, breach of confidentiality, or unauthorized access to the system.
To work on all aspects of internal safety and to prevent all data leaks from the system

We checked the environment for compliance with OWASP, NIST, and ISO 27001 cyber security standards and tested it for vulnerabilities
In the process of testing web resources for vulnerability, the WEZOM team relies upon OWASP, NIST, PCI DSS, and other standards. This aspect depends on the client’s needs.

The team collected information about the architecture and components of the platform, conducted active scanning, analyzed potential vulnerabilities, and performed manual testing for false positives.
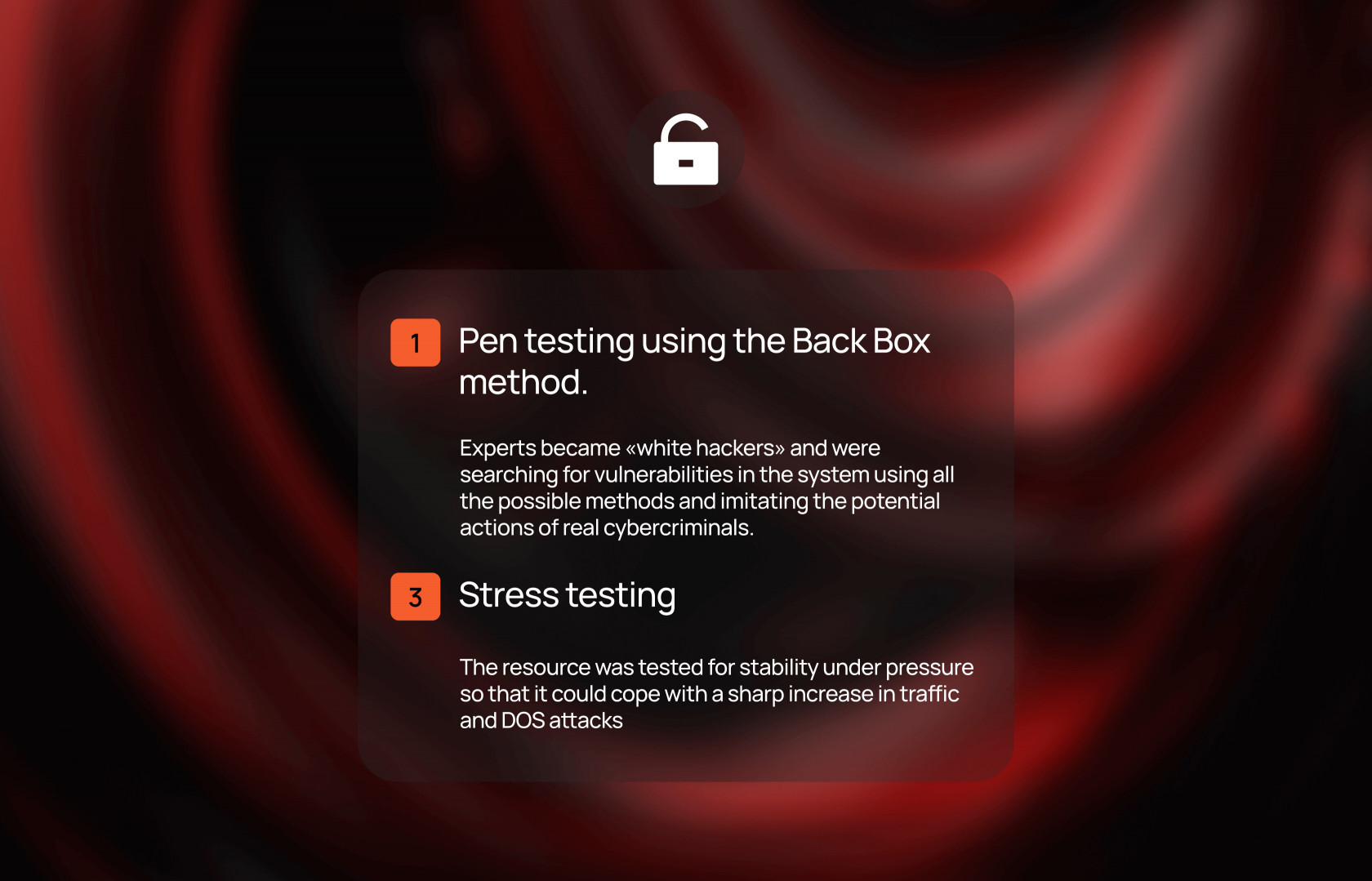
Experts became «white hackers» and were searching for vulnerabilities in the system using all the possible methods and imitating the potential actions of real cybercriminals.
The resource was tested for stability under pressure so that it could cope with a sharp increase in traffic and DOS attacks
We detected a range of problems and vulnerabilities in the client’s system. They were prioritized fixed and then retested. The testing for pressure has given us the advantage of making the platform robust enough for intense traffic increases and DDoS attacks.The WEZOM team has given the client the full report on the results of the analysis and introduced additional cybersecurity-ensuring steps. They included providing constant monitoring and repeated checks of the system.
This meant that the main results of the project included the minimization of risks, and providing a new cybersecurity strategy to protect the client’s business for the years ahead.