Knowing about the cybersecurity threats in the oil&gas industry, and what constitutes oil software security, we can protect ourselves in a far better way and be more resilient to potential threats that are only expanding. Therefore, knowledge of security measures, together with its application, is a brilliant weapon in the fight against cybercrime and various types of attacks.
And if we talk about the security of specific software solutions, then there are special technological security measures for them, and we will understand their work as well. Let's see how cybersecurity for oil and gas works, and what effective tools can be used to achieve a sufficient level of safety within your company. We will also touch on the different trends in the oil and gas industry that relate to cyber safety.
Let's have a look.
The Infrastructure of a Typical Oil and Gas Company
To know more about the oil and gas industry and the issues related to cybersecurity in this field, it is worth knowing what the infrastructures within companies look like. The companies’ work and their security needs depend on these infrastructures and this is exactly why we need to know the mechanisms of their work. Now let’s have a look at some of the details.
If we talk about the infrastructure of companies in the oil and gas industry, then the product chain of such a company is usually divided into three main stages – these are upstream, midstream, and downstream.
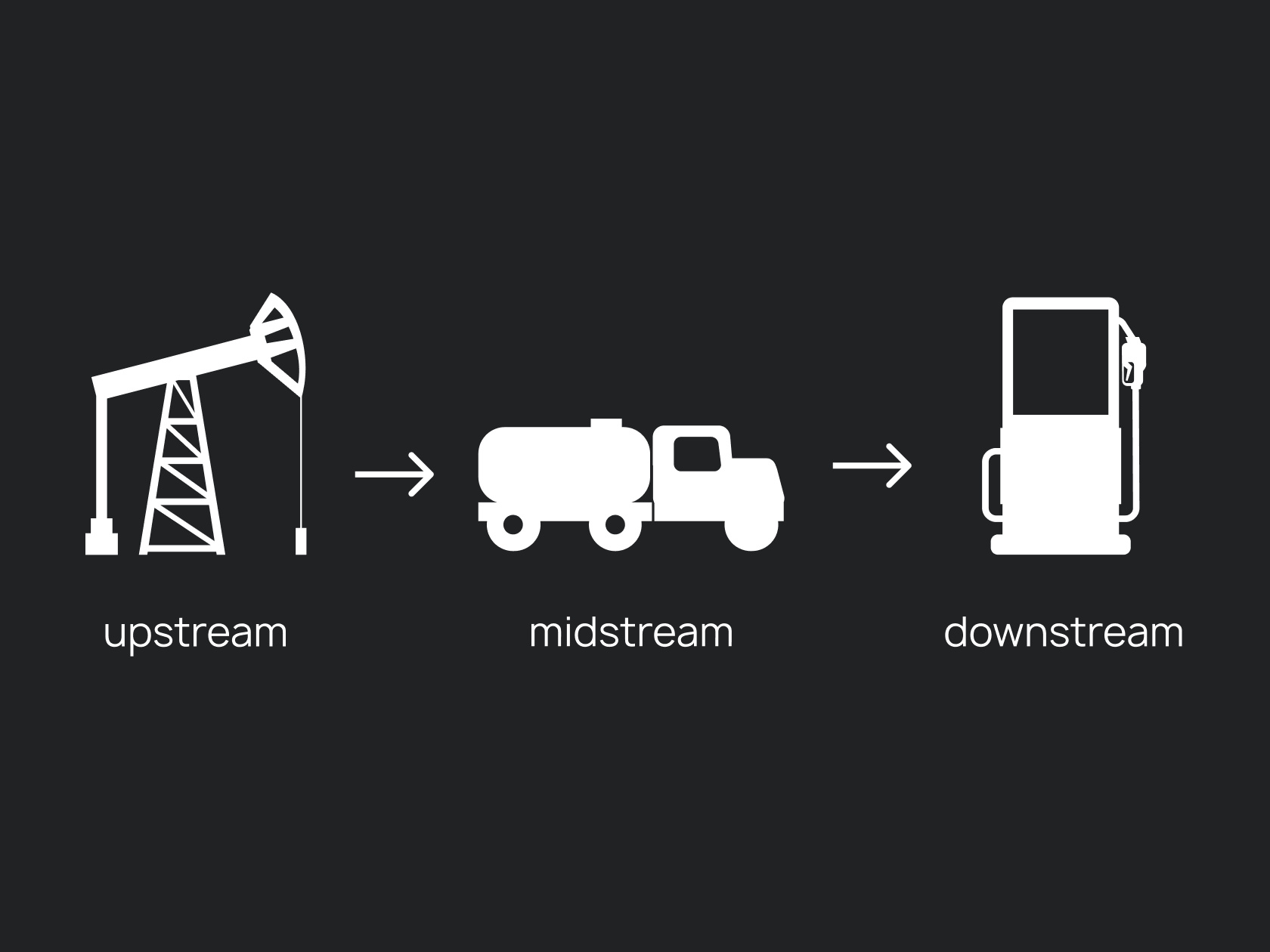
Upstream is the part that includes such aspects as oil exploration and production, and midstream is what is connected with the processes of transportation and storage of crude oil. And, finally, downstream is all the processes associated with the direct production of the final product.
The Three Main Parts of the Companies’ Work
All three of these parts make up the infrastructure of companies in the oil and gas industry, and all of them can be at risk from a cybersecurity point of view.
Companies in the industry have production sites where crude oil is extracted from wells, tank farms, and where oil is stored temporarily, and transportation systems specifically designed to transport oil to a refinery. There are various modes of transportation.
How Hackers Can Hack the Oil&Gas Industry Via ERP Systems
In general, hackers can utilize the ERP systems of the oil and gas companies’ corporate networks and exploit the weaknesses thus sabotaging pipeline pressure or hiding oil spills. Using ERP solutions to hack gas companies is one of the easiest ways to exploit software solutions. This is a fairly common type of threat. By exploiting the weaknesses of ERP applications used in the industrial sector, hackers can achieve their goals quite easily.
As for the weaknesses that may be present in your ERP, some of the particular examples may include vulnerable legacy technologies that enterprise resource planning systems commonly use, and in this aspect, issues may arise.
If earlier it was believed that only Stuxnet-type attacks were possible, now such cases are not uncommon. This means that ERPs still have some common cybersecurity gaps that need to be addressed.
Some of the vulnerabilities within an ERP system may include the solutions themselves being soft targets. As enterprise resource planning systems have large amounts of the company’s valuable data, as well as employee information, they must be protected with careful attention. Other aspects that may be overlooked include:
- Missing software patches.
- Some of the flaws within the ERP system authentication mechanism.
- Low network visibility.
These flaws occur often and within different companies, and this is exactly why they should be considered as these are not some minor details.
The Cost of Energy Companies Doing Nothing with Cyber Attacks
Energy companies need to boost their cybersecurity levels already, as the danger is real. Now, with the development of various technologies, threats from the point of view of cybersecurity are only becoming more common, so simple protection is no longer enough - we need training that will not leave cybercrime any chance and make the company completely protected. At the same time, the concern for cybersecurity within various systems subject to vulnerability falls entirely on the company itself.
Many attackers want to take advantage of vulnerabilities, because this is an easy and relatively effective way, and these dangers must be anticipated and anticipated. These efforts must be undertaken directly by the company.
The Value of a Custom ERP for Cybersecurity
It is advisable to invest in a custom ERP system to improve security. This step will enable your enterprise resource planning system to not only better meet your needs but also to protect you more effectively.
Therefore, we recommend that you consider the possibility of creating custom software for at least these reasons. You can read more in our article about the implementation of the ERP system.
How Do We, as Developers, Make Sure the Code Is Good
There are certain principles that the WEZOM team regularly uses in their work to improve the level of quality and make sure that everything in the project goes exactly as intended.
Our company has special methods that help us in our work and are proven by practice because our clients solve their problems effectively thanks to the innovative technologies that we offer. We have prepared some helpful information that will help you find answers to some of the main questions about software security.
When it comes to code quality, there is a certain procedure WEZOM prefers to use. It involves code review in the process of code receiving as one of the most fundamental steps. Also, among other parameters of quality, the code is being checked for readability, maintainability, and so on. It is also checked for compliance with development standards.
In this process, we are often supported by automation tools that allow for faster, more precise processes, and also always include unit tests in our work. Also, we use static code analysis tools which can be used in the analysis of source code or compiled versions of code. Static code analysis tools, or SAST tools, check the code without actually running it and allow you to foresee a certain percentage of potential errors.
Other tools that are included in our work involve data profiling tools that help WEZOM specialists reduce potential productivity issues, and linters that assist us in finding minor issues and in detecting possible non-compliance with standards. Automated approach is more precise in this case as it allows for reduced mistakes, and this is exactly why we use plugins for linting.
In addition to the above-mentioned points, when the code is covered with unit tests, we use coverage analysis tools. This step helps us to evaluate the general quality of the product.
Bug tracking and defect tracking tools are commonly used in such cases, but we follow this tendency to improve our efficiency and ensure the quality of our code is maximum. In our case, this mostly concerns working with programs such as Jira and Youtrack (often used in the process of bug tracking), however, such work is maximally integrated into other processes.
Our last, but not the least, point is the integration with CI/CD. We follow the build-test-run principle and use continuous automated testing.
Who Is Responsible for Code Security in Our Team?
Several distributed development teams are working on the project simultaneously. The project architecture, which is a microservice, allows us to do this work. Each team is autonomous within its product modules for which it is responsible and has a classic scheme: front and back specialists with their technical leads.
Code security is the responsibility of each member of the development team when they are working on their tasks. Technical leads monitor compliance with security principles, including: checking input data, using secure libraries and frameworks, ensuring the security of the code execution environment, and having automatic security tests.
And as for code security, it commonly includes shared responsibility. And while the developers are responsible for their work — i. e. For writing a secure code (including code validation and encryption), sec ops are responsible for detecting the potential security risks and DevSecOps are responsible for other aspects of security. QA engineers are also responsible for scanning, pen testing and the use of testing tools such as OWASP ZAP.
The general approach to the responsibility for code security includes various tools and processes, including static analysis tools. In addition to detecting mistakes, they can highlight certain weaknesses the code has. It may be buffer overflow, SQL injections, and other issues.
It also uses dynamic code analysis. We - again - check the code for potential vulnerabilities and perform penetration testing, but on an already running application. This step also includes manual code review, which is of the utmost importance. And fuzz testing, as part of E2E tests, allows you to increase the efficiency of an already running application, because end-to-end testing checks whether all system components can work in real scenarios.
Another important aspect is that we also use dependency scanning and shared libraries from 3rd party distributors in our code. You may have heard of this technique in connection with a well-known Log4J vulnerability that allows an attacker to remotely run arbitrary Java code to take control of the target Java server. There can be a lot of such dependencies in an application, both in third-party libraries and in Docker images on which the application is built. Dependency scanning allows us to find all the bottlenecks in the code and potential vulnerabilities that we need to respond to: update the version of the dependency, apply a patch, assess vulnerability risks, etc.
And the last aspect that is of paramount importance for code security is compliance checks. Without this certification, and if our product does not comply with standards (for example, PCI DSS, ISO or GDPR), then we will not be able to release the application, so we also pay special attention to this step.
How Do We Check Code Security: 4 Levels of Quality Control
Let’s discuss the process that involves the expert responsible for security making sure that the code is high-quality and safe. In other words: let’s talk about how we usually check code security. As an example: within the company, there is a chain for checking code quality and we have 4 levels of quality control complexity.
Tell us briefly about each of them.
The team usually takes the following measures to maintain code security:
- Using proven frameworks and libraries that ensure security – this step significantly reduces the total number of vulnerabilities.
- Conducting code security audits. Regular code audits by technical leads allow you to identify and eliminate vulnerabilities.
- Static code analyzers are also commonly used by our team. These tools are used to check the code for vulnerabilities.
- The security of the code execution environment is ensured. For example, it can be done by restricting access rights.
- Educating and training developers on secure coding also reduces the number of developer-created vulnerabilities.
- We use automated security tests that detect vulnerabilities that may have been missed manually.
Code Security
As for the code quality, we believe it lies in a properly designed architecture, and we also adhere to development standards, all code is covered by tests, code reviews, and automatic and manual testing are implemented in our work.
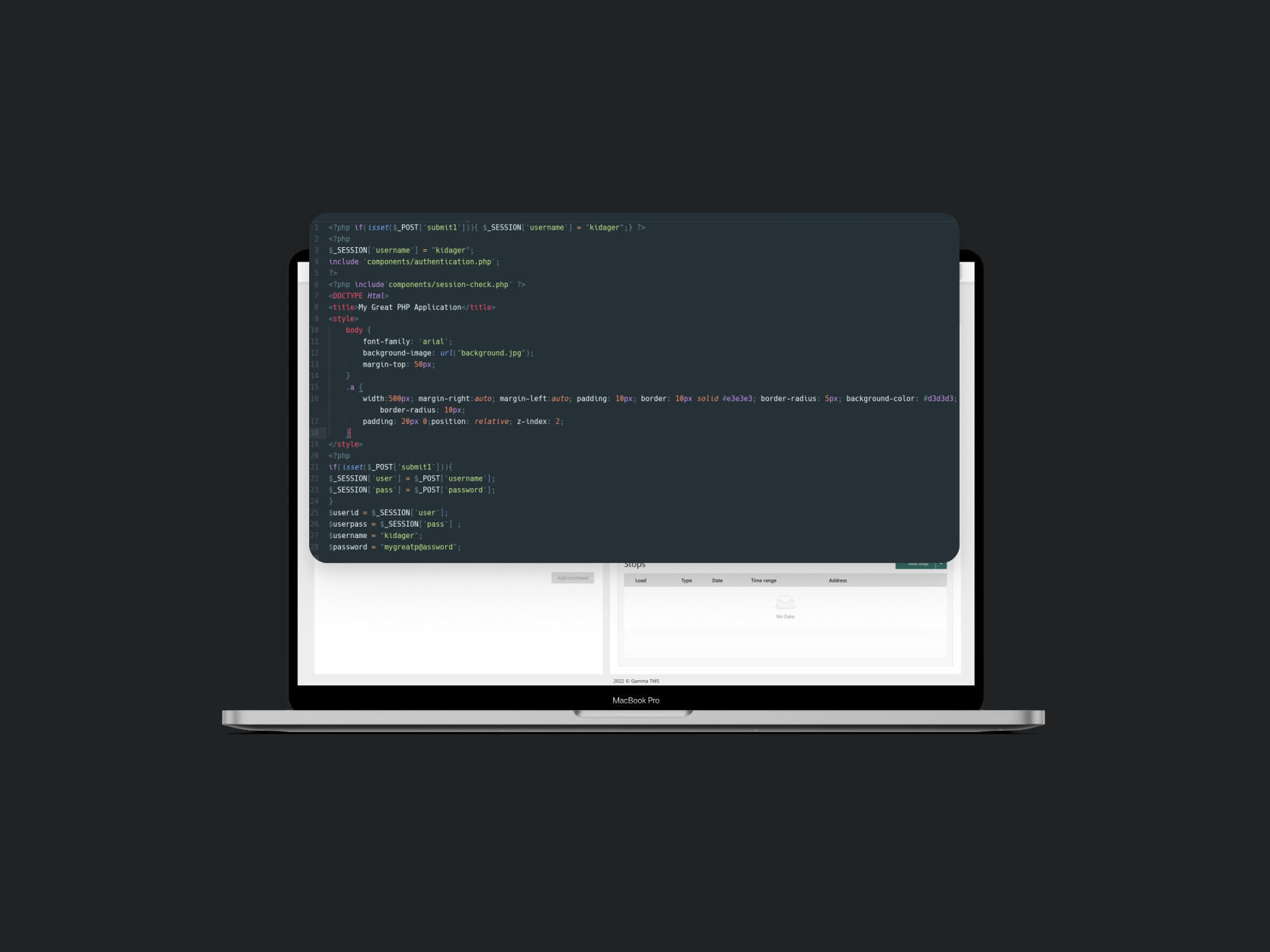
The principles for ensuring our team has quality code include:
- Quality architecture development: A well-designed architecture helps produce clean, maintainable, and extensible code. Development technicians are responsible for the architecture of the project.
- Use of standards and best practices: Our developers must adhere to standards and best practices to ensure consistency and interoperability in code.
- Also, the use of automatic code-checking tools, such as the static code analyzers I mentioned earlier and tests, are a must - they help identify errors and flaws in the code.
- The team performs code reviews. It is a procedure where the code is reviewed by other developers, it helps to identify errors, flaws, and potential problems in the code.
- Learning and Feedback: Our developers must constantly learn and receive feedback from their peers to improve their code and learn new best practices.
- It is also important for us that the development team adheres to the principles of SOLID (Single Responsibility, Open-Closed, Liskov Substitution, Interface Segregation, Dependency Inversion)
Conclusion
To conclude, safety is often our sole responsibility. If you understand that your company and the systems it uses at work are at risk in terms of cybersecurity, then you now know that there are various tools to increase protection, and many of them will be effective in your particular case.
Of course, the level of security of a particular software solution plays a big role in oil and gas security, so choosing custom software development can make your task much easier and make your company much more protected and resistant to possible cyber attacks on oil and gas companies.
Therefore, when choosing options, pay attention to the opportunities and options presented in the field of custom software development and choose the best options for yourself.
